| 21.1. NAT resource | ||
|---|---|---|
 | Chapter 21. NAT - Network Address Translation |  |
Abilis implements NAT (Network Address Translation) with PAT (Port Address Translation) and IPACL (IP Access Control List) services.
By properly specifying:
source IP address or network;
destination IP address or network;
source UDP/TCP port;
destination UDP/TCP port;
Source/Destination IP resource;
TOS (Type of Service) for packets priority management by services.
A high level of security is granted.
![[Note]](../images/note.png) | Note |
|---|---|
Abilis isn't a Firewall! It implements basic firewall function, but evolved features must be commissioned to a “real” firewall. Abilis and firewall can coexist with no problems. |
ABILIS has 4 NAT zones: INside, OUTside, VPN, DMZ.
The relationships between the IP router and the NAT functional unit can be represented schematically as follows:
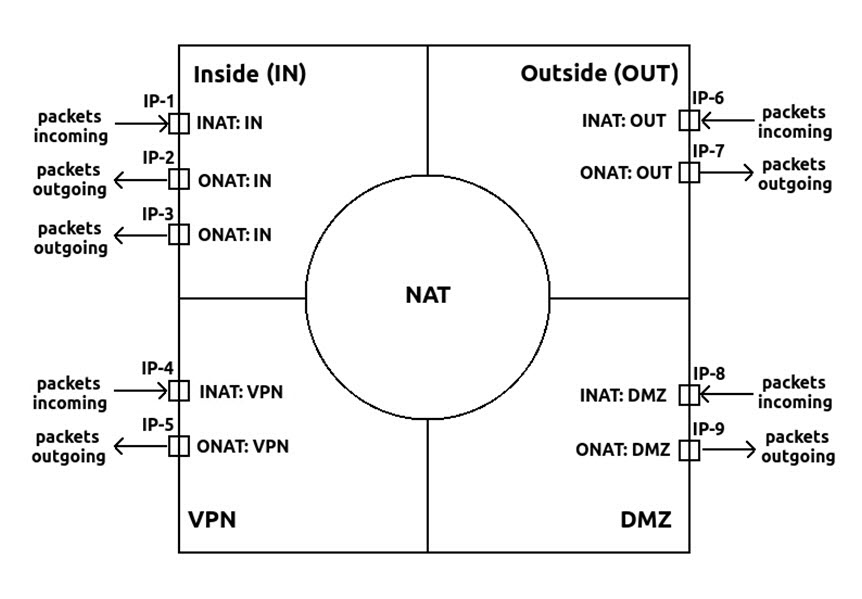
The NAT table contains rules of descending priority
PR:0,
PR:1, ... (the first rule,
PR:0, is the one which is checked
first):
[15:20:49] ABILIS_CPX:d nat
UPNP maps not present
Configured maps
-------------------------------------------------------------------------------
PR: [DESCR:]
INAT: ADD: SNET: DNET: ANET:
ONAT: SPO: DPO: APO: PAT:
SIP: DIP: PROT: TOUT:
-------------------------------------------------------------------------------
0 IN SRC 192.168.000.000/24 * OUT-IP
OUT * * AUTO YES
-------------------------------------------------------------------------------
1 VPN DST * 010.000.011.000/24 192.168.000.000/24
IN * * * YES
-------------------------------------------------------------------------------
2 OUT SRC 212.002.038.222/32 088.081.001.165/32 192.168.000.178/32
IN * 8001 http(80) YES
3 1 * SYS
-------------------------------------------------------------------------------
![[Important]](../images/important.png) | Important |
|---|---|
These rules only apply to packets which enter the router through
a port which belongs to a different zone, with respect to the IP port
used to go out. In other words, in order to have packets processed by
NAT, the values of |
The rules contain both the packets selection criteria and the kind of desired processing:
Packet-selection
When the IP packet does not match the specifications of a rule, the rule is skipped; the next rule will be immediately checked.
When a rule matches the IP packet's specs, the address/port processing specified in the rule itself is executed.
The rule's parameters used to select the IP packets are:
The zone through which packets enter
into the IP router. In our example IP-1, IP-2 and
IP-3 have their NAT parameter set to INSIDE.
If the purpose is to select packets incoming through the port
IP-1, then the selection criterion is
INAT:INSIDE.
The zone where packets shall leave
the IP router. If packets have to be sent-out of the
router through a port marked with
NAT:OUTSIDE, then the
right criterion is
ONAT:OUTSIDE.
The IP-packet's source network, by means of the
SNET parameter (“source network”). For
example
SNET:192.168.0.0/24.
The IP-packet's destination address, by means of the
DNET parameter (“destination network”). For
example, DNET:* if every
possible destination-network is concerned.
The filtering specified with the INAT
parameter can be further restricted by specifying the
SIP, source IP port
(SIP:1 for IP-1). The rule
will be applied only if the packet's source port is actually the
one specified with SIP.
The filtering specified with the ONAT
parameter can be further restricted by specifying the
DIP, destination IP port
(DIP:5 for IP-5).
When the protocol is TCP or UDP, the filtering can by
further restricted by specifying the SPO,
source port (for example
SPO:25).
When the protocol is TCP or UDP, the filtering can by
further restricted by specifying the DPO,
destination port (for example
DPO:25).
When the Port Address Translation is enabled, the
selection criterion can also define PROT the
protocol in use: ICMP, TCP, UDP, * (all).
Packet processing
Once the IP-packet fulfils all the selection criteria specified in a rule, it is processed according to the specs written in the rule itself.
Please mind: the NAT table is scanned twice:
The first scan is reserved for the rules which request the
processing of the destination address
(ADD:DST).
The second scan is reserved to the rules which request the
processing of the source address
(ADD:SRC).
In the first scan, this is the applied processing:
The selected DESTINATION address is changed as specified
in the “alias network”, described by the ANET
parameter. For instance:
ANET:88.81.111.22/32.
When the protocol is TCP or UDP and PAT
(port address translation) is active
(PAT:YES), it is also
possible to define the change of the DESTINATION port. The
target port is defined in the APO (alias
port) parameter.
In the second scan, this is the applied processing:
The selected SOURCE address is changed as specified in the
“alias network”, described by the ANET
parameter. For instance:
ANET:OUT-IP makes all the
packets use the current public IP-address in use for the output
port.
When the protocol is TCP or UDP and PAT
(port address translation) is active
(PAT:YES), it is also
possible to define the change of the SOURCE port. The target
port is defined in the APO (alias port)
parameter.
![[Important]](../images/important.png) | Important |
|---|---|
Frequent mistakes:
|
Inside. The set of networks, there's subject of translation, usually “private” networks.
Outside. All other networks, usually “public” addresses located on the Internet.
Inside local IP address. The IP address which was assigned to a host on the inside network.
Inside global IP address. The
IP address of an inside host as it appears to the outside networks.
If, as usual, the outside network is the Internet, the address must
be one of the “public” addresses which the ISPs have
assigned to the user's router for those connections. In the table of
NAT Aliases this term called as ANET:.
Processed IP packet. It means in this packet was changed a source or destination address in some cases a source or destination port was changed too.
Ignored IP packet. It means that this packet wasn't changed.
Static Address Translation. The user can establish a one-to-one mapping between the inside local and global addresses, which happens when the number (netmask) of inside local and global addresses are identical.
Dynamic Source Address Translation. The user can establish a dynamic mapping between the inside and global addresses, which happens when the number (netmask) of inside local and global addresses are different.
Port Address Translation (PAT). The user can save addresses in the global address pool by allowing source ports in TCP connections or UDP conversations to be translated. Different local addresses will be mapped to the same global address, with port translation providing the necessary uniqueness for TCP/UDP and other tricks providing uniqueness for ICMP.
Extended filtering in PAT mode. The purpose of this feature is to allow a selective activation of the PAT translation based on the destination TCP/UDP port and on the IP protocol, with the result that network managers can empower their control of the network by:
Granting access only to some service, e.g. WEB and FTP.
Blocking access only to specific services, e.g. RealAudio / RealVideo servers.
Precisely distinguishing inbound connections from outbound ones.
Allowing internal users to access ANY service on the Internet while outside users may access only a restricted set.
Destination port mapping. This behavior is very useful in many situations, the most frequents are:
The user has just one public IP address and on the internal LAN there are more computers with several IP addresses running different services that must be reached from outside, e.g. FTP, HTTP, SMTP etc.
The user has just one public IP address and on the internal LAN there are more computers with several IP addresses running the same service with different contents, e.g. a commercial web, a technical web, a restricted access web.
Add the resource to the Abilis system with the command:
[11:01:39] ABILIS_CPX:a res:nat
RES:NAT ALREADY EXISTSThe NAT resource may already exist in the system, but may not yet be active: set it active with the command:
[11:01:48] ABILIS_CPX:s act res:nat
COMMAND EXECUTED![[Caution]](../images/caution.png) | Caution |
|---|---|
After adding or setting the NAT active, you must restart the Abilis to make the resource running (use the command warm start to reboot the Abilis). |
[11:01:39] ABILIS_CPX:s p nat act:yesCOMMAND EXECUTED [11:01:39] ABILIS_CPX:d p natRES:Nat - Not Saved (SAVE CONF), Not Refreshed (INIT) ------------------------- Run DESCR:Network_Address_Translator LOG:DS ACT:YES dimtable:1000 DNS-ALG:NO SNMP-ALG:NO PPTP-ALG:NO IKE-AWARE:NO NAT-LOOPBACK:NO - Not PAT mode parameters ---------------------------------------------- TOUT:3600 - PAT mode parameters -------------------------------------------------- FRAG:5 ICMP:5 DNS:5 SNMP:5 SNTP:5 UDP-OPENING:5 UDP-CONN:180 TCP-OPENING:5 TCP-CONN:360 TCP-CLOSING:15 TCP-CLOSED:1 TCP-RST:YES PPTP-CONN:360 INSIDE-MIL:NOLIMIT OUTSIDE-MIL:NOLIMIT VPN-MIL:NOLIMIT DMZ-MIL:NOLIMIT MIL-TIME:2
Use the following command to display resource parameters; the command d p nat ? displays the meaning of all parameters.
[11:01:39] ABILIS_CPX:d p nat
Run DESCR:Network_Address_Translator
LOG:DS ACT:YES dimtable:1000
DNS-ALG:NO SNMP-ALG:NO PPTP-ALG:NO IKE-AWARE:NO
NAT-LOOPBACK:NO
- Not PAT mode parameters ----------------------------------------------
TOUT:3600
- PAT mode parameters --------------------------------------------------
FRAG:5 ICMP:5 DNS:5 SNMP:5 SNTP:5
UDP-OPENING:5 UDP-CONN:180
TCP-OPENING:5 TCP-CONN:360 TCP-CLOSING:15 TCP-CLOSED:1
TCP-RST:YES PPTP-CONN:360
INSIDE-MIL:NOLIMIT OUTSIDE-MIL:NOLIMIT VPN-MIL:NOLIMIT DMZ-MIL:NOLIMIT
MIL-TIME:2Meaning of the most important parameters:
LOGLogging functionalities activation/deactivation.
ACTNAT runtime activation/deactivation.
dimtableIt specifies how many translations can be created at the same time.
DNS-ALGEnable/disable DNS Application Level Gateway [NO, YES].
SNMP-ALGEnable/disable SNMP Application Level Gateway [NO, YES].
PPTP-ALGEnable/disable PPTP Application Level Gateway [NO, YES].
IKE-AWAREEnable/disable IKE awareness. Minimise remap of UDP ports 500 and 4500 [NO, YES].
NAT-LOOPBACKEnable/disable the packets loopback for destination translations [NO, YES]. NAT loopback permits the access of a service via the public IP address from inside the local network.
![[Tip]](../images/tip.png) | Tip |
|---|---|
Interesting chapter: Section 71.15, “How to configure the NAT loopback”. |
TOUTThis value sets the timeout of static and dynamic translations, i.e. those created without the PAT mode. If the translation isn't used for the specified time (i.e. no packets need it), it times out and it has removed by the translation table.
FRAGTime-out for linkable fragment identifier [1..240 sec].
ICMPTime-out for ICMP link type [1..240 sec].
DNSTime-out for DNS link type [1..240 sec].
SNMPTime-out for SNMP link type [1..240 sec].
SNTMPTime-out for SNTP link type [1..240 sec].
UDP-OPENINGTime-out for UDP links in Opening state [1..240 sec].
UDP-CONNTime-out for UDP links in Connected state [60..65535 sec].
TCP-OPENINGTime-out for TCP links in Opening state [1..240 sec].
TCP-CONNTime-out for TCP links in Connected state [60..65535 sec].
TCP-CLOSINGTime-out for TCP links in Closed state [1..240 sec].
TCP-RSTEnable sending of RESET for expired links [NO, YES].
PPTP-CONNTime-out for PPTP links in Connected state [60..65535 sec].
INSIDE-MILMaximal number of links that same IP address on INSIDE interface can open at the same time [NOLIMIT, 1..10000].
OUTSIDE-MILMaximal number of links that same IP address on OUTSIDE interface can open at the same time [NOLIMIT, 1..10000].
VPN-MILMaximal number of links that same IP address on VPN interface can open at the same time [NOLIMIT, 1..10000].
DMZ-MILMaximal number of links that same IP address on DMZ interface can open at the same time [NOLIMIT, 1..10000].
MIL-TIMEResync time used for maximal initiator links procedure [2..30 sec].
The following command allows the administrator to change the configuration of the resource:
s p nat parameter:value...
![[Caution]](../images/caution.png) | Caution |
|---|---|
To activate the changes made on the upper case parameters, execute the initialization command init nat; while to set act the changes made on the lowercase parameters a save conf and an Abilis restart are required (i.e. With warm start command). |